Access Control Systems
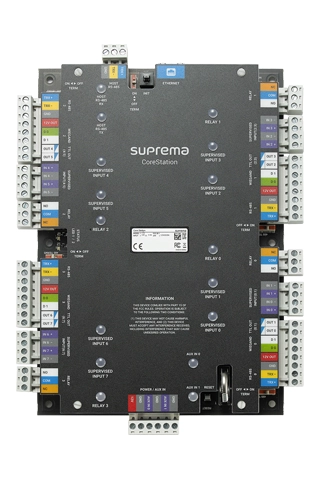
Elite International offers robust and scalable Access Control Systems tailored for enterprises, government institutions, and industrial facilities. Our solutions are designed to protect assets, regulate personnel movement, and ensure secure access across your organization’s premises.
We provide a wide range of technologies including:
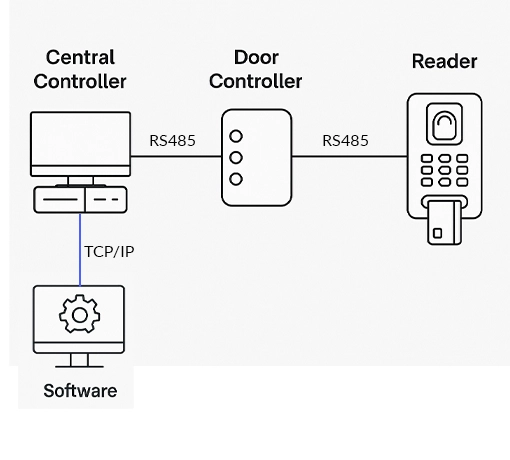
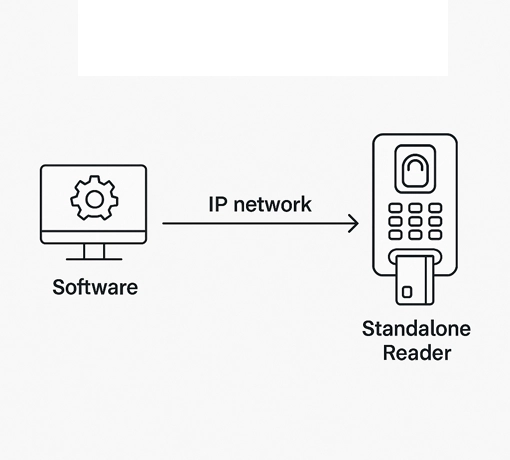
- IP-Based Distributed Access Control Systems
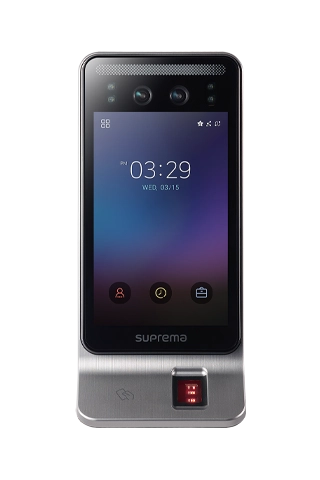
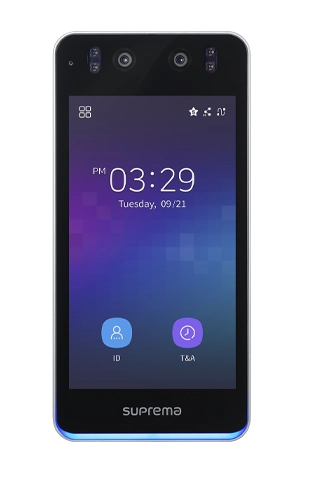
- Biometric Authentication: Facial Recognition, Fingerprint, Iris
- RFID, QR Code, and Mobile Access
- Integration with Time & Attendance, Fire Alarm, and Security Systems
Whether it's a single entry point or a multi-site deployment, our systems ensure centralized management, real-time monitoring, and detailed access logs — empowering your organization with complete visibility and control.