Access Control - Systems
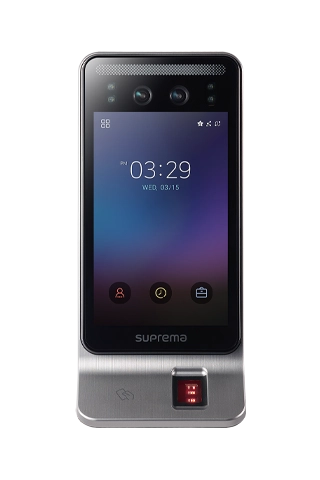
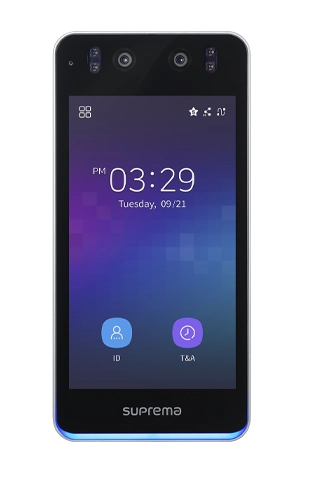
Biometrics Replaces the Need for Keys, Fobs and Pin Codes. Your Finger and Face Become the Key to Your Business.
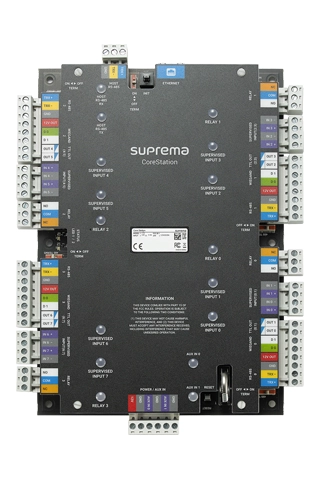
Elite Offers A Complete Range of Security Solutions with Unrivalled Matching Speed, Accuracy and Level of Security Incorporating A Combination of Biometric and Traditional Card and Proximity Readers, Giving You the Flexibility to Mix and Match to Suit Your Needs